
 It is perhaps one of the C.I.A.’s most mischievous secrets.
It is perhaps one of the C.I.A.’s most mischievous secrets.“Kryptos,” the sculpture nestled in a courtyard of the agency’s Virginia headquarters since 1990, is a work of art with a secret code embedded in the letters that are punched into its four panels of curving copper.
“Our work is about discovery — discovering secrets,” said Toni Hiley, director of the C.I.A. Museum. “And this sculpture is full of them, and it still hasn’t given up the last of its secrets.”
Not for lack of trying. For many thousands of would-be code crackers worldwide, “Kryptos” has become an object of obsession. Dan Brown has even referred to it in his novels.
The code breakers have had some success. Three of the puzzles, 768 characters long, were solved by 1999, revealing passages — one lyrical, one obscure and one taken from history. But the fourth message of “Kryptos” — the name, in Greek, means “hidden” — has resisted the best efforts of brains and computers.
And Jim Sanborn, the sculptor who created “Kryptos” and its puzzles, is getting a bit frustrated by the wait. “I[..]umed the code would be cracked in a fairly short time,” he said, adding that the intrusions on his life from people who think they have solved his fourth puzzle are more than he expected.
So now, after 20 years, Mr. Sanborn is nudging the process along. He has provided The New York Times with the answers to six letters in the sculpture’s final passage. The characters that are the 64th through 69th in the final series on the sculpture read NYPVTT. When deciphered, they read BERLIN.
But there are many steps to cracking the code, and the other 91 characters and their proper order are yet to be determined.
“Having some letters where we know what they are supposed to be could be extremely valuable,” said Elonka Dunin, a computer game designer who runs the most popular “Kryptos” Web page.
None of this was really envisioned when the Central Intelligence Agency planned the expansion known as the New Headquarters Building in the 1980s and asked artists to submit proposals to create a work of art for the courtyard. The broad principles it provided for the $250,000 commission included the notion that it should “engender feelings of well-being, hope.”
The winner was Mr. Sanborn, and the agency introduced him to Edward Scheidt, a retiring C.I.A. cryptographer, who gave him a crash course in the arts of concealing text and helped devise the codes used in the sculpture.
One reason the fourth puzzle has proved so difficult is because, with just 97 characters, it is shorter than any but the first. Longer chunks of text are easier to crack because there is more information to study for patterns.

 The messages form the two left-hand panels of the sculpture’s wall of text; the other two panels on the right side provide the key to cracking some of the text. Each is encrypted in a different way from the others.
The messages form the two left-hand panels of the sculpture’s wall of text; the other two panels on the right side provide the key to cracking some of the text. Each is encrypted in a different way from the others.The first reads: “Between subtle shading and the absence of light lies the nuance of iqlusion.” (Mr. Sanborn admitted to introducing misspellings to add a degree of difficulty.)
The second passage includes the latitude and longitude of the C.I.A.’s headquarters and asks, “Does Langley know about this? They should: it’s buried out there somewhere. X Who knows the exact location? Only WW.”
This is a reference to William Webster, the former C.I.A. chief — Mr. Sanborn gave him a key to deciphering the messages.
The third passage paraphrases, with an intentional misspelling, the account of Howard Carter, the renowned Egyptologist, as he opened King Tut’s tomb. Mr. Sanborn has said the passage has inspired him since childhood.
“Slowly, desparatly slowly, the remains of passage debris that encumbered the lower part of the doorway was removed. With trembling hands I made a tiny breach in the upper left-hand corner. And then, widening the hole a little, I inserted the candle and peered in. The hot air escaping from the chamber caused the flame to flicker, but presently details of the room within emerged from the mist. x Can you see anything? q”
Though “Kryptos” has long been famous in code-busting circles, it gained wider notoriety when Mr. Brown slyly referred to it on the dust jacket of his best-selling novel “The DaVinci Code” and incorporated it into the plot of “The Lost Symbol.”

 While many artists might be thrilled with such publicity, Mr. Sanborn was deeply irked by the way his work was portrayed as a possible key to “ancient Masonic secrets” in “The Lost Symbol.”
While many artists might be thrilled with such publicity, Mr. Sanborn was deeply irked by the way his work was portrayed as a possible key to “ancient Masonic secrets” in “The Lost Symbol.”“As far as I’m concerned, he did me no favors,” Mr. Sanborn groused about Mr. Brown.
The message of his artwork, and its relevance to the C.I.A., is more nuanced than a plot point in a potboiler novel, he said.
“Anybody holding a secret has a position of power, even if it’s a trivial secret,” Mr. Sanborn said.
To code breakers, Mr. Sanborn, not the C.I.A., is in the real position of power. They e-mail him. They call him. Some have produced papers of 100 pages or more explaining their theories on the final 97 characters. “In their world, a complete tour de force,” said Mr. Sanborn, save for one thing: “It doesn’t have anything to do with ‘Kryptos.’ ”
He likes and respects many of the fans. But some others? “Certifiable,” he said.
Recently, one even showed up in the front yard of his home on an island in the Chesapeake Bay, brandishing a three-ring binder that she was convinced contained the answer. It did not.
He has asked a friend — Mr. Sanborn has given him some of the answers, but not all — to handle inquiries from those who say they have solved the puzzle.
“My friend says, ‘What do you have in letter-position 27?’ ” Mr. Sanborn explained. “If that’s not the same letter, ‘Game over, and you didn’t crack the code.’ ” (He recently set up a Web site to take submissions automatically.)
So far, no one has had more than two letters right, though some dispute this. “They say, of course I cracked the code — who are you to say I didn’t crack the code?” Mr. Sanborn said. Some of them even suggest that he does not know the answer himself.
He hopes others will hurry up and solve it.
“I can’t do this for many more decades, O.K.?” Mr. Sanborn said. “I’m 65 now. They might get some more clues at 75. But 85?”
Found Here: http://slumz.boxden.com/f5/nov-22-can-you-crack-c-i-s-kryptos-code-1451559/

 Mystery Crypto Letter Has Coders Stumped
Mystery Crypto Letter Has Coders StumpedA coded letter sent last year to the Fermi National Accelerator Laboratory in Illinois has the lab, and outside coders stumped. The letter was sent anonymously last March in a hand-addressed envelope via regular mail to the physics lab’s public affairs office.
After sitting on the letter for more than a year, the lab posted it on a physics blog in May, hoping to get help cracking it.
Thousands of sleuths have taken a stab at it so far and have succeeded to crack two parts of the letter. An engineer at the Canadian Space Center used a variation of the base-3 system to uncover a line that reads “Frank Shoemaker would call this noise,” which refers to an 86-year-old retired Princeton University physicist who helped design the magnets used with the lab’s first particle accelerator, known as the Main Ring. Another line in the letter has been cracked to read, “Employee number basse sixteen.”
A Chicago Tribune story about the letter offers some possible explanations behind the two sentences and what appears to be a typo in the second sentence.
But, like the famous CIA Kryptos sculpture (which also has a typo), one final section of the letter (pictured above) remains unsolved. The lab is hoping outsiders will help them unravel the clues. You can see the entire letter on the physics blog where it was posted. An undated update to the blog post indicates that they suspect they now know who may have sent the letter.
Coders post your solutions in the comments section below or send them directly to me (you’ll find my e-mail address in this blog’s righthand column) with an explanation about how you cracked it.
Found Here: http://www.wired.com/threatlevel/2008/07/mystery-at-ferm/
Sanborn was born in 1945 in Washington, D.C. His father, a print maker, was the Director of Exhibitions at the Library of Congress for 30 years. His mother was a pianist and photo researcher. Sanborn grew up in Alexandria, Virginia, attended JEB Stuart High School in Fairfax, and went on to study archaeology and Romanesque cathedrals. He studied archaeology at Oxford University, and received a Bachelor of Arts degree in paleontology, fine arts, and social anthropology in 1968 from Randolph-Macon College in Ashland Virginia, and a Master of Fine Arts degree in sculpture from Pratt Institute in Brooklyn in 1971. He taught at Montgomery College in Rockville, and for nine years was the artist-in-residence and taught classes at Glen Echo Park. He has also traveled extensively in Asia, and in 1983 was commissioned to install a piece in Japan.
Mr. Sanborn is noted for his work with American stone and related materials that evoke a sense of mystery and the forces of nature. He is probably best known for the "Kryptos" sculpture installed at CIA Headquarters in 1990, which displays encrypted messages which continue to stump code-breakers to this day.
Sanborn contact info: This website is not directly associated with Mr. Sanborn.
Found Here: http://elonka.com/kryptos/sanborn.html






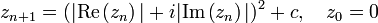
 which will either escape or remain bounded. The difference between this calculation and that for the
which will either escape or remain bounded. The difference between this calculation and that for the 


























